The Chrome team had announced plans to roll out a change in the default behavior of the SameSite functionality starting in a release of Chrome version 78 Beta on October 18, 2019. This rollout will be moved to Chrome version 80 release on February 4, 2020. Workaround through Chrome In Chrome 80 there is an option which will allow you to revert to the legacy cookie behavior. This will be available for at least 12 months after the release of Chrome 80 stable. Refer to SameSite Updates for more information. Workaround Steps for Case: 1 App cookie. There are some upcoming changes being rolled out to chrome in Jan 2020 involving default behavior of the samesite property in cookies, effectively making 3rd party cookies disabled by default. This can be tested now in chrome 76/77 by enabling the feature flags: go to chrome://flags search for sa. Chrome (as of v76), treats all cookies as Lax if SameSite attribute is absent or its value isn't set. This setting effectively restricts them to be used only within the first-party context by default and makes it possible to automatically shut down any external access attempts. Reviewing SameSite warnings in Google Chrome (Click to play) If you find these errors, it means that Chrome, in early February 2020, and other browsers, eventually, will stop allowing 3rd party site scripts to set/read cookies on your site if the 3rd party does not explicitly state that the cookie should be allowed cross site, and handled securely.
It's Time To Properly Secure Your Cookies
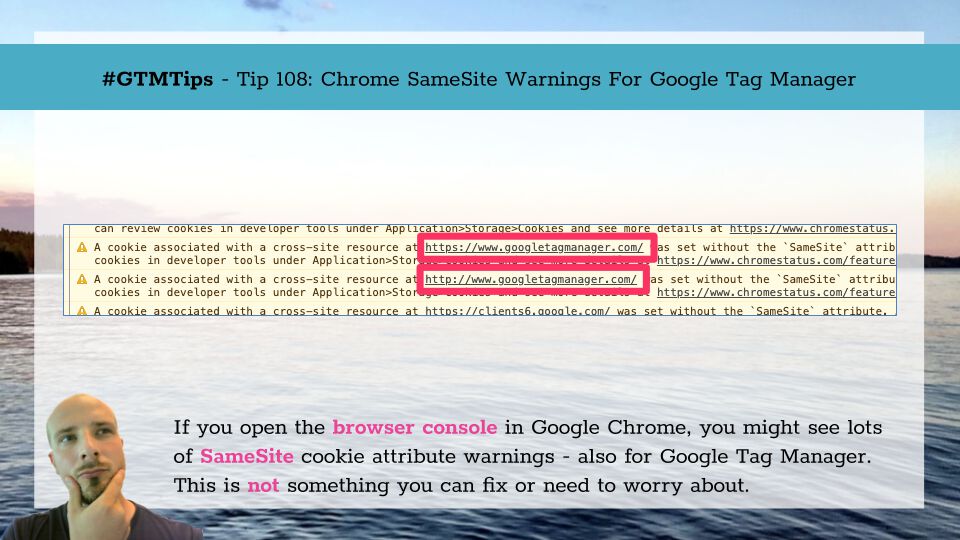
Google Chrome browser recently began displaying two warnings inside of its JavaScript Console related to the upcoming changes in cross-site cookie delivery policy. What are these alerts trying to achieve and how exactly does this affect your website?
The first type of warning refers to a missing SameSite attribute on any of the cookies currently attached to the session:
A cookie associated with a cross-site resource at was set without the `SameSite` attribute. A future release of Chrome will only deliver cookies with cross-site requests if they are set with `SameSite=None` and `Secure`. You can review cookies in developer tools under Application>Storage>Cookies and see more details at https://www.chromestatus.com/feature/5088147346030592 and https://www.chromestatus.com/feature/5633521622188032.
The second type of warning calls attention to third-party cookies with SameSiteattribute correctly set to None but without required Secure flag attached to them:
A cookie associated with a resource at (cookie domain) was set with `SameSite=None` but without `Secure`. A future release of Chrome will only deliver cookies marked `SameSite=None` if they are also marked `Secure`. You can review cookies in developer tools under Application>Storage>Cookies and see more details at https://www.chromestatus.com/feature/5633521622188032.
While at the moment both messages are merely a heads up for developers, changes come into effect quite soon – to be exact, in Chrome v80, which is slated for a stable release in February, 2020.
In the next two sections, I'll briefly explain the relevant terms and explore the background for introducing this new behaviour. If you'd like to find out how this may or may not affect your website straight away, feel free to skip to ‘Consequences for your website' section below.
Quick Refresher On Definitions
SameSite and Secure are attributes which belong to Set-Cookie HTTP header. Secure is a standalone boolean value indicating that a cookie must be passed only over a protected connection (HTTPS), whilst SameSite can be equal to one of the following values:
Strict
Cookie will only be sent if the site for the cookie matches the site currently shown in the user's browser URL bar.
Lax
Allows the cookie to be included along with top-level navigations. For instance, following through a link from another website leading to your domain.
None
Explicitly marks the cookie for cross-domain usage. As of Chrome v80, this value must go hand in hand with Secure attribute to ensure encrypted transmission.
Intentions Behind The Change
The absence of the SameSite attribute causes the vast majority of cookies to be sent in a cross-site context, regardless of the actual intent. This poses certain problems for users and developers alike:
- Browsers have no way of distinguishing between same-site and cross-site cookies, which confines the usefulness of cookie controls. If you erase cookies, everything is wiped completely – including legitimate things like login states and website preferences.
- The majority of anti-tracking tools offer an option to block all third-party cookies. If no proper
SameSiteattribute is set or is missing altogether, they will inadvertently shut down first-party cookies too. Websites are tethered as a result and you are more likely to run into various malfunctions. On top of that, this blanket approach to blocking of undesired cookies, to no small degree, subverts privacy by incentivizing cagey techniques such as fingerprinting. - Third-party cookies are widely used for tracking and may contain sensitive data that pertains to user identity. Delivering cookies through non-secure connections facilitates eavesdropping as intruders can easily intercept and, what's worse, tamper with such requests. In other words, being exposed to CSRF attacks is a status-quo for many developers these days.
Folks at Google put forward a proposal for a set of open standards called ‘Incrementally Better Cookies' with an intention to fundamentally enhance privacy on the web. The change calls to explicitly define which cookies are permitted to function across foreign domains and encourages embeddable content producers to migrate to HTTPS. This adjustment mitigates certain class of security concerns – specifying SameSiteattribute is a reasonably robust protection against CSRF and cross-site injection attacks. It also grants users more granular control over cookies, allowing them to preserve useful settings while doing a cleanup. Last but not least, browsers will be able to distinctly identify and list sites that are setting cross-site cookies.
Consequences For Your Website
Same-(sub)domain cookies
If you manage cookies that are only accessed by the same domain or any related subdomains, there is no action required on your part. Chrome (as of v76), treats all cookies as Lax if SameSite attribute is absent or its value isn't set. This setting effectively restricts them to be used only within the first-party context by default and makes it possible to automatically shut down any external access attempts.
Nevertheless, it's strongly recommended to clearly mark you same-domain cookies as either Lax or Strict, as stock browser behavior cannot be relied upon – not all browsers offer the same protection as Chrome does.
Cross-domain cookies
If you currently provide a service that other sites consume, such as advertising or widgets, you will have to do a make-over to comply with the new standard. First of all, you should use SameSite=None attribute along with Secure https://hkqax.over-blog.com/2021/02/armed-forces-laser-sight-module-manual.html. flag to clearly communicate your intentions about using a cookie in a third-party context. You also need to ensure that your requests are being carried strictly over HTTPS.
Mixed context
Finally, If you have cookies meant to be accessed in both first and third-party context, consider separating them to accrue the security benefits of SameSite=Lax setting.
How To Prepare If You Are Affected?
When making changes to the way you are handling cookies on the server, keep in mind that it's highly desirable to maintain backward compatibility.
Example of a new Set-Cookie header definition:
There are two strategies at your disposal:
- Specify both old and new style cookies simultaneously. Arrange for graceful degradation. The downside of this approach is that every request will be carrying redundant cookies.
- Detect client via User Agent string before sending the
Set-Cookieheader. While more efficient, beware that some affected clients could slip through the cracks.
In this repo you'll find examples on implementing SameSite=None; Secure attributes in a variety of languages, libraries, and frameworks.
How To Test Things Out Right Now
Chrome and Firefox, at the moment of writing, are the only browsers offering experimental support for this feature.
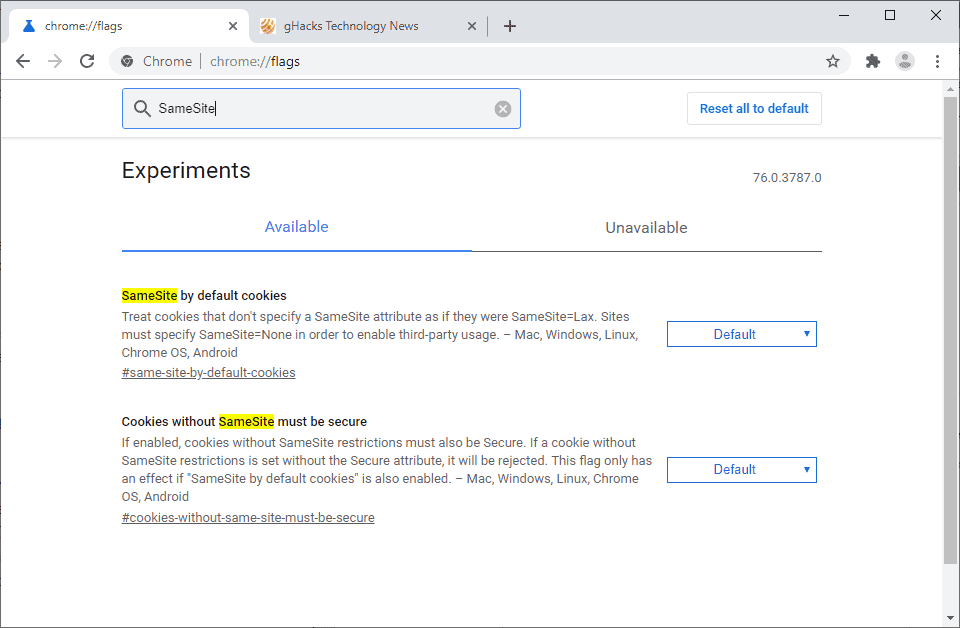
Chrome (v76+)
- Go to
chrome://flags/and search forsamesite - Enable the following flags:
same-site-by-default-cookiecookies-without-same-site-must-be-secure
Firefox (v69+)
- Go to
about:configand search forsamesite - Turn on the following flags:
network.cookie.sameSite.laxByDefaultnetwork.cookie.sameSite.noneRequiresSecure
Conclusion
Stricter SameSite cookie policy aims at improving both privacy and security of the web platform. This is an example of a simple yet powerful change which rapidly became a widespread standard. Hopefully, we will see all major browser vendors continue on their path towards safer, surveillance-resistant web.
Coview: Making Customer Support Effortless
When your web app user is having problems, Coview lets you request a screenshot, a screen recording – or lets you jump right into a co-browsing session with them.
- There's nothing for your users to download or install.
- Users are never tracked without their knowledge.
- No need for them to try and explain the problem – they can just show you.
But best of all, Coview records the entire action at a code level. Free slots online google. Meaning you can pause and explore the page as it is in that moment – including being able to inspect code right in the recording.
- Resolve bugs without having to reproduce them
- The source HTML and other code remains unmodified
- Javascript errors are shown with their complete stack trace
- Detailed network performance reports included
This means you can get on with solving issues without having to rely on your non-technical customers to try and explain the error.
Try Coview for free
SameSite cookies explained
For implementation advice on SameSite=None, see part 2:SameSite cookie recipes
Cookies are one of the methods available for adding persistent state to websites. Over the years their capabilities have grown and evolved, but left theplatform with some problematic legacy issues. To address this, browsers(including Chrome, Firefox, and Edge) are changing their behavior to enforcemore privacy-preserving defaults.
Each cookie is a key=value pair along with a number of attributes that controlwhen and where that cookie is used. You've probably already used theseattributes to set things like expiration dates or indicating the cookie shouldonly be sent over HTTPS. Servers set cookies by sending the aptly-namedSet-Cookie header in their response. For all the detail you can dive intoRFC6265bis,but for now here's a quick refresher. Mac powerpoint design ideas.
Say you have a blog where you want to display a 'What's new' promo to yourusers. Users can dismiss the promo and then they won't see it again for a while.You can store that preference in a cookie, set it to expire in a month(2,600,000 seconds), and only send it over HTTPS. That header would look likethis:
When your reader views a page that meets those requirements, i.e. they're on asecure connection and the cookie is less than a month old, then their browserwill send this header in its request:
You can also add and read the cookies available to that site in JavaScript usingdocument.cookie. Making an assignment to document.cookie will create oroverride a cookie with that key. For example, you can try the following in yourbrowser's JavaScript console:
Reading document.cookie will output all the cookies accessible in the currentcontext, with each cookie separated by a semicolon:
If you try this on a selection of popular sites you will notice that most ofthem set significantly more than just three cookies. In most cases, thosecookies are sent on every single request to that domain, which has a number ofimplications. Upload bandwidth is often more restricted than download for yourusers, so that overhead on all outbound requests is adding a delay on your timeto first byte. Be conservative in the number and size of cookies you set. Makeuse of the Max-Age attribute to help ensure that cookies don't hang aroundlonger than needed.
What are first-party and third-party cookies? #
If you go back to that same selection of sites you were looking at before, youprobably noticed that there were cookies present for a variety of domains, notjust the one you were currently visiting. Cookies that match the domain of thecurrent site, i.e. what's displayed in the browser's address bar, are referredto as first-party cookies. Similarly, cookies from domains other than thecurrent site are referred to as third-party cookies. This isn't an absolutelabel but is relative to the user's context; the same cookie can be eitherfirst-party or third-party depending on which site the user is on at the time.
Continuing the example from above, let's say one of your blog posts has apicture of a particularly amazing cat in it and it's hosted at/blog/img/amazing-cat.png. Because it's such an amazing image, another personuses it directly on their site. If a visitor has been to your blog and has thepromo_shown cookie, then when they view amazing-cat.png on the otherperson's site that cookie will be sent in that request for the image. Thisisn't particularly useful for anyone since promo_shown isn't used for anythingon this other person's site, it's just adding overhead to the request.
If that's an unintended effect, why would you want to do this? It's thismechanism that allows sites to maintain state when they are being used in athird-party context. For example, if you embed a YouTube video on your site thenvisitors will see a 'Watch later' option in the player. If your visitor isalready signed in to YouTube, that session is being made available in theembedded player by a third-party cookie—meaning that 'Watch later' button willjust save the video in one go rather than prompting them to sign in or having tonavigate them away from your page and back over to YouTube.
One of the cultural properties of the web is that it's tended to be open bydefault. This is part of what has made it possible for so many people to createtheir own content and apps there. However, this has also brought a number ofsecurity and privacy concerns. Cross-site request forgery (CSRF) attacks rely onthe fact that cookies are attached to any request to a given origin, no matterwho initiates the request. For example, if you visit evil.example then it cantrigger requests to your-blog.example, and your browser will happily attachthe associated cookies. If your blog isn't careful with how it validates thoserequests then evil.example could trigger actions like deleting posts or addingtheir own content.
Users are also becoming more aware of how cookies can be used to track theiractivity across multiple sites. However until now there hasn't been a way toexplicitly state your intent with the cookie. Your promo_shown cookie shouldonly be sent in a first-party context, whereas a session cookie for a widgetmeant to be embedded on other sites is intentionally there for providing thesigned-in state in a third-party context.
The absence of the SameSite attribute causes the vast majority of cookies to be sent in a cross-site context, regardless of the actual intent. This poses certain problems for users and developers alike:
- Browsers have no way of distinguishing between same-site and cross-site cookies, which confines the usefulness of cookie controls. If you erase cookies, everything is wiped completely – including legitimate things like login states and website preferences.
- The majority of anti-tracking tools offer an option to block all third-party cookies. If no proper
SameSiteattribute is set or is missing altogether, they will inadvertently shut down first-party cookies too. Websites are tethered as a result and you are more likely to run into various malfunctions. On top of that, this blanket approach to blocking of undesired cookies, to no small degree, subverts privacy by incentivizing cagey techniques such as fingerprinting. - Third-party cookies are widely used for tracking and may contain sensitive data that pertains to user identity. Delivering cookies through non-secure connections facilitates eavesdropping as intruders can easily intercept and, what's worse, tamper with such requests. In other words, being exposed to CSRF attacks is a status-quo for many developers these days.
Folks at Google put forward a proposal for a set of open standards called ‘Incrementally Better Cookies' with an intention to fundamentally enhance privacy on the web. The change calls to explicitly define which cookies are permitted to function across foreign domains and encourages embeddable content producers to migrate to HTTPS. This adjustment mitigates certain class of security concerns – specifying SameSiteattribute is a reasonably robust protection against CSRF and cross-site injection attacks. It also grants users more granular control over cookies, allowing them to preserve useful settings while doing a cleanup. Last but not least, browsers will be able to distinctly identify and list sites that are setting cross-site cookies.
Consequences For Your Website
Same-(sub)domain cookies
If you manage cookies that are only accessed by the same domain or any related subdomains, there is no action required on your part. Chrome (as of v76), treats all cookies as Lax if SameSite attribute is absent or its value isn't set. This setting effectively restricts them to be used only within the first-party context by default and makes it possible to automatically shut down any external access attempts.
Nevertheless, it's strongly recommended to clearly mark you same-domain cookies as either Lax or Strict, as stock browser behavior cannot be relied upon – not all browsers offer the same protection as Chrome does.
Cross-domain cookies
If you currently provide a service that other sites consume, such as advertising or widgets, you will have to do a make-over to comply with the new standard. First of all, you should use SameSite=None attribute along with Secure https://hkqax.over-blog.com/2021/02/armed-forces-laser-sight-module-manual.html. flag to clearly communicate your intentions about using a cookie in a third-party context. You also need to ensure that your requests are being carried strictly over HTTPS.
Mixed context
Finally, If you have cookies meant to be accessed in both first and third-party context, consider separating them to accrue the security benefits of SameSite=Lax setting.
How To Prepare If You Are Affected?
When making changes to the way you are handling cookies on the server, keep in mind that it's highly desirable to maintain backward compatibility.
Example of a new Set-Cookie header definition:
There are two strategies at your disposal:
- Specify both old and new style cookies simultaneously. Arrange for graceful degradation. The downside of this approach is that every request will be carrying redundant cookies.
- Detect client via User Agent string before sending the
Set-Cookieheader. While more efficient, beware that some affected clients could slip through the cracks.
In this repo you'll find examples on implementing SameSite=None; Secure attributes in a variety of languages, libraries, and frameworks.
How To Test Things Out Right Now
Chrome and Firefox, at the moment of writing, are the only browsers offering experimental support for this feature.
Chrome (v76+)
- Go to
chrome://flags/and search forsamesite - Enable the following flags:
same-site-by-default-cookiecookies-without-same-site-must-be-secure
Firefox (v69+)
- Go to
about:configand search forsamesite - Turn on the following flags:
network.cookie.sameSite.laxByDefaultnetwork.cookie.sameSite.noneRequiresSecure
Conclusion
Stricter SameSite cookie policy aims at improving both privacy and security of the web platform. This is an example of a simple yet powerful change which rapidly became a widespread standard. Hopefully, we will see all major browser vendors continue on their path towards safer, surveillance-resistant web.
Coview: Making Customer Support Effortless
When your web app user is having problems, Coview lets you request a screenshot, a screen recording – or lets you jump right into a co-browsing session with them.
- There's nothing for your users to download or install.
- Users are never tracked without their knowledge.
- No need for them to try and explain the problem – they can just show you.
But best of all, Coview records the entire action at a code level. Free slots online google. Meaning you can pause and explore the page as it is in that moment – including being able to inspect code right in the recording.
- Resolve bugs without having to reproduce them
- The source HTML and other code remains unmodified
- Javascript errors are shown with their complete stack trace
- Detailed network performance reports included
This means you can get on with solving issues without having to rely on your non-technical customers to try and explain the error.
Try Coview for free
SameSite cookies explained
For implementation advice on SameSite=None, see part 2:SameSite cookie recipes
Cookies are one of the methods available for adding persistent state to websites. Over the years their capabilities have grown and evolved, but left theplatform with some problematic legacy issues. To address this, browsers(including Chrome, Firefox, and Edge) are changing their behavior to enforcemore privacy-preserving defaults.
Each cookie is a key=value pair along with a number of attributes that controlwhen and where that cookie is used. You've probably already used theseattributes to set things like expiration dates or indicating the cookie shouldonly be sent over HTTPS. Servers set cookies by sending the aptly-namedSet-Cookie header in their response. For all the detail you can dive intoRFC6265bis,but for now here's a quick refresher. Mac powerpoint design ideas.
Say you have a blog where you want to display a 'What's new' promo to yourusers. Users can dismiss the promo and then they won't see it again for a while.You can store that preference in a cookie, set it to expire in a month(2,600,000 seconds), and only send it over HTTPS. That header would look likethis:
When your reader views a page that meets those requirements, i.e. they're on asecure connection and the cookie is less than a month old, then their browserwill send this header in its request:
You can also add and read the cookies available to that site in JavaScript usingdocument.cookie. Making an assignment to document.cookie will create oroverride a cookie with that key. For example, you can try the following in yourbrowser's JavaScript console:
Reading document.cookie will output all the cookies accessible in the currentcontext, with each cookie separated by a semicolon:
If you try this on a selection of popular sites you will notice that most ofthem set significantly more than just three cookies. In most cases, thosecookies are sent on every single request to that domain, which has a number ofimplications. Upload bandwidth is often more restricted than download for yourusers, so that overhead on all outbound requests is adding a delay on your timeto first byte. Be conservative in the number and size of cookies you set. Makeuse of the Max-Age attribute to help ensure that cookies don't hang aroundlonger than needed.
What are first-party and third-party cookies? #
If you go back to that same selection of sites you were looking at before, youprobably noticed that there were cookies present for a variety of domains, notjust the one you were currently visiting. Cookies that match the domain of thecurrent site, i.e. what's displayed in the browser's address bar, are referredto as first-party cookies. Similarly, cookies from domains other than thecurrent site are referred to as third-party cookies. This isn't an absolutelabel but is relative to the user's context; the same cookie can be eitherfirst-party or third-party depending on which site the user is on at the time.
Continuing the example from above, let's say one of your blog posts has apicture of a particularly amazing cat in it and it's hosted at/blog/img/amazing-cat.png. Because it's such an amazing image, another personuses it directly on their site. If a visitor has been to your blog and has thepromo_shown cookie, then when they view amazing-cat.png on the otherperson's site that cookie will be sent in that request for the image. Thisisn't particularly useful for anyone since promo_shown isn't used for anythingon this other person's site, it's just adding overhead to the request.
If that's an unintended effect, why would you want to do this? It's thismechanism that allows sites to maintain state when they are being used in athird-party context. For example, if you embed a YouTube video on your site thenvisitors will see a 'Watch later' option in the player. If your visitor isalready signed in to YouTube, that session is being made available in theembedded player by a third-party cookie—meaning that 'Watch later' button willjust save the video in one go rather than prompting them to sign in or having tonavigate them away from your page and back over to YouTube.
One of the cultural properties of the web is that it's tended to be open bydefault. This is part of what has made it possible for so many people to createtheir own content and apps there. However, this has also brought a number ofsecurity and privacy concerns. Cross-site request forgery (CSRF) attacks rely onthe fact that cookies are attached to any request to a given origin, no matterwho initiates the request. For example, if you visit evil.example then it cantrigger requests to your-blog.example, and your browser will happily attachthe associated cookies. If your blog isn't careful with how it validates thoserequests then evil.example could trigger actions like deleting posts or addingtheir own content.
Users are also becoming more aware of how cookies can be used to track theiractivity across multiple sites. However until now there hasn't been a way toexplicitly state your intent with the cookie. Your promo_shown cookie shouldonly be sent in a first-party context, whereas a session cookie for a widgetmeant to be embedded on other sites is intentionally there for providing thesigned-in state in a third-party context.
Explicitly state cookie usage with the SameSite attribute #
The introduction of the SameSite attribute (defined inRFC6265bis)allows you to declare if your cookie should be restricted to a first-party orsame-site context. It's helpful to understand exactly what 'site' means here.The site is the combination of the domain suffix and the part of the domain justbefore it. For example, the www.web.dev domain is part of the web.dev site.
Key Term:
If the user is on www.web.dev and requests an image from static.web.dev thenthat is a same-site request.
The public suffix list defines this, so it's notjust top-level domains like .com but also includes services like github.io.That enables your-project.github.io and my-project.github.io Photo mechanic 5 0 – quality digital camera image browser. to count asseparate sites.
Key Term:
If the user is on your-project.github.io and requests an image frommy-project.github.io that's a cross-site request.
Introducing the SameSite attribute on a cookie provides three different waysto control this behaviour. You can choose to not specify the attribute, or youcan use Strict or Lax to limit the cookie to same-site requests.
If you set SameSite to Strict, your cookie will only be sent in afirst-party context. In user terms, the cookie will only be sent if the site forthe cookie matches the site currently shown in the browser's URL bar. So, if thepromo_shown cookie is set as follows:
When the user is on your site, then the cookie will be sent with the request asexpected. However when following a link into your site, say from another site orvia an email from a friend, on that initial request the cookie will not be sent.This is good when you have cookies relating to functionality that will alwaysbe behind an initial navigation, such as changing a password or making apurchase, but is too restrictive for promo_shown. If your reader follows thelink into the site, they want the cookie sent so their preference can beapplied.
That's where SameSite=Lax comes in by allowing the cookie to be sent withthese top-level navigations. Let's revisit the cat article example from abovewhere another site is referencing your content. They make use of your photo ofthe cat directly and provide a link through to your original article.
And the cookie has been set as so:
When the reader is on the other person's blog the cookie will not be sentwhen the browser requests amazing-cat.png. However when the reader follows thelink through to cat.html on your blog, that request will include thecookie. This makes Lax a good choice for cookies affecting the display of thesite with Strict being useful for cookies related to actions your user istaking.
Caution:
Neither Strict nor Lax are a complete solution for your site's security.Cookies are sent as part of the user's request and you should treat them thesame as any other user input. That means sanitizing and validating the input.Never use a cookie to store data you consider a server-side secret.
Fu dao le slot machine how to win. Finally there is the option of not specifying the value which has previouslybeen the way of implicitly stating that you want the cookie to be sent in allcontexts. In the latest draft ofRFC6265bis thisis being made explicit by introducing a new value of SameSite=None. This meansyou can use None to clearly communicate that you intentionally want the cookiesent in a third-party context.
If you provide a service that other sites consume such as widgets, embeddedcontent, affiliate programs, advertising, or sign-in across multiple sitesthen you should use None to ensure your intent is clear.
Changes to the default behavior without SameSite #
While the SameSite attribute is widely supported, it has unfortunately notbeen widely adopted by developers. The open default of sending cookieseverywhere means all use cases work but leaves the user vulnerable to CSRF andunintentional information leakage. To encourage developers to state their intentand provide users with a safer experience, the IETF proposal,Incrementally Better Cookieslays out two key changes:
- Cookies without a
SameSiteattribute will be treated asSameSite=Lax. - Cookies with
SameSite=Nonemust also specifySecure, meaning they requirea secure context.
Chrome implements this default behavior as of version 84.Firefoxhas them available to test as of Firefox 69 and will make them default behaviorsin the future. To test these behaviors in Firefox, openabout:config and setnetwork.cookie.sameSite.laxByDefault.Edgealso plans to change its default behaviors.
This article will be updated as additional browsers announce support.
SameSite=Lax by default #
While this is intended to apply a more secure default, you should ideally set anexplicit SameSite attribute rather than relying on the browser to apply thatfor you. This makes your intent for the cookie explicit and improves the chancesof a consistent experience across browsers.
Caution:
The default behaviour applied by Chrome is slightly more permissive than anexplicit SameSite=Lax as it will allow certain cookies to be sent on top-levelPOST requests. You can see the exact details onthe blink-dev announcement.This is intended as a temporary mitigation, you should still be fixing yourcross-site cookies to use SameSite=None; Secure.
SameSite=None must be secure #
You can test this behavior as of Chrome 76 by enablingchrome://flags/#cookies-without-same-site-must-be-secure and from Firefox 69in about:config by settingnetwork.cookie.sameSite.noneRequiresSecure.
You will want to apply this when setting new cookies and actively refreshexisting cookies even if they are not approaching their expiry date.
If you rely on any services that provide third-party content on your site, youshould also check with the provider that they are updating their services. Youmay need to update your dependencies or snippets to ensure that your site picksup the new behavior.
Both of these changes are backwards-compatible with browsers that have correctlyimplemented the previous version of the SameSite attribute, or just do notsupport it at all. By applying these changes to your cookies, you are makingtheir intended use explicit rather than relying on the default behavior of thebrowser. Likewise, any clients that do not recognize SameSite=None as of yetshould ignore it and carry on as if the attribute was not set.
Warning:
A number of older versions of browsers including Chrome, Safari, and UC browserare incompatible with the new None attribute and may ignore or restrict thecookie. This behavior is fixed in current versions, but you should check yourtraffic to determine what proportion of your users are affected. You can see thelist of known incompatible clients on the Chromium site.
SameSite cookie recipes #
For further detail on exactly how to update your cookies to successfully handlethese changes to SameSite=None and the difference in browser behavior, head tothe follow up article, SameSite cookie recipes.
Kind thanks for contributions and feedback from Lily Chen, Malte Ubl, MikeWest, Rob Dodson, Tom Steiner, and Vivek Sekhar
Samesite Cookie Chrome 80
Cookie hero image byPille-Riin PriskeonUnsplash

